Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Computers & Internet Heartbleed
- Thread starter Gasometer
- Start date
- Tagged users None
I don't understand that at all, so not really.
Only by the poor quality of this thread
- Mar 25, 2003
- 35,681
- 28,334
For those unaware SSL (Secure Sockets Layer) is a form of cryotgraphy use to transport data across a network - most commonly the internet. If you are communicating with a web site over SSL you'll notice HTTPS (as opposed to HTTP) in the browser. Your bank, facebook, twitter or any web site with any sort of decent revenue should be using SSL. Essentially what happens is when you access a site all the data that gets sent back and forth will be encrypted. When it gets to other end it will be decrypted and either displayed by your web browser, or processed by the web server depending on which direction the data is going.
When a website doesn't use SSL (such as bigfooty) all the data that gets sent across the network will be in plaintext. This data includes your username and password when you enter it. If someone was to run a program like wireshark which is able to watch traffic that passes through any network it's connected to. And yes this works, I've run wireshark on my home network and logged onto bigfooty and was able to see my username and password in amongst the data.
I really can't make it any less technical than that.
So yeah it's a pretty concerning issue for anyone who values their privacy... but most people don't so it will pass over 95% of people. SSL is one of the cornerstones of Internet Security and given how many people have relied on it for security it's a bit of a worry because it's really not known how exploited this bug was (maybe it was hardly exploited at all).
I always push for the open source community so it's disappointing that this has happened, but in some respects it shows the value of the Open Source community because they were able to pick it up - albeit extremely delayed.
Companies who use proprietary SSL software... It may be secure, it may not be. There is just no way for people to know so you're purely relying on them to be honest in their dealings.
When a website doesn't use SSL (such as bigfooty) all the data that gets sent across the network will be in plaintext. This data includes your username and password when you enter it. If someone was to run a program like wireshark which is able to watch traffic that passes through any network it's connected to. And yes this works, I've run wireshark on my home network and logged onto bigfooty and was able to see my username and password in amongst the data.
I really can't make it any less technical than that.
So yeah it's a pretty concerning issue for anyone who values their privacy... but most people don't so it will pass over 95% of people. SSL is one of the cornerstones of Internet Security and given how many people have relied on it for security it's a bit of a worry because it's really not known how exploited this bug was (maybe it was hardly exploited at all).
I always push for the open source community so it's disappointing that this has happened, but in some respects it shows the value of the Open Source community because they were able to pick it up - albeit extremely delayed.
Companies who use proprietary SSL software... It may be secure, it may not be. There is just no way for people to know so you're purely relying on them to be honest in their dealings.
- Thread starter
- #6
For those unaware SSL (Secure Sockets Layer) is a form of cryotgraphy use to transport data across a network - most commonly the internet. If you are communicating with a web site over SSL you'll notice HTTPS (as opposed to HTTP) in the browser. Your bank, facebook, twitter or any web site with any sort of decent revenue should be using SSL. Essentially what happens is when you access a site all the data that gets sent back and forth will be encrypted. When it gets to other end it will be decrypted and either displayed by your web browser, or processed by the web server depending on which direction the data is going.
When a website doesn't use SSL (such as bigfooty) all the data that gets sent across the network will be in plaintext. This data includes your username and password when you enter it. If someone was to run a program like wireshark which is able to watch traffic that passes through any network it's connected to. And yes this works, I've run wireshark on my home network and logged onto bigfooty and was able to see my username and password in amongst the data.
I really can't make it any less technical than that.
So yeah it's a pretty concerning issue for anyone who values their privacy... but most people don't so it will pass over 95% of people. SSL is one of the cornerstones of Internet Security and given how many people have relied on it for security it's a bit of a worry because it's really not known how exploited this bug was (maybe it was hardly exploited at all).
I always push for the open source community so it's disappointing that this has happened, but in some respects it shows the value of the Open Source community because they were able to pick it up - albeit extremely delayed.
Companies who use proprietary SSL software... It may be secure, it may not be. There is just no way for people to know so you're purely relying on them to be honest in their dealings.
LOL, thank god you understand it.
Do you think our true identities will be revealed on BF?

- Apr 26, 2007
- 4,777
- 2,650
- AFL Club
- Essendon
For those unaware SSL (Secure Sockets Layer) is a form of cryotgraphy use to transport data across a network - most commonly the internet. If you are communicating with a web site over SSL you'll notice HTTPS (as opposed to HTTP) in the browser. Your bank, facebook, twitter or any web site with any sort of decent revenue should be using SSL. Essentially what happens is when you access a site all the data that gets sent back and forth will be encrypted. When it gets to other end it will be decrypted and either displayed by your web browser, or processed by the web server depending on which direction the data is going.
When a website doesn't use SSL (such as bigfooty) all the data that gets sent across the network will be in plaintext. This data includes your username and password when you enter it. If someone was to run a program like wireshark which is able to watch traffic that passes through any network it's connected to. And yes this works, I've run wireshark on my home network and logged onto bigfooty and was able to see my username and password in amongst the data.
I really can't make it any less technical than that.
So yeah it's a pretty concerning issue for anyone who values their privacy... but most people don't so it will pass over 95% of people. SSL is one of the cornerstones of Internet Security and given how many people have relied on it for security it's a bit of a worry because it's really not known how exploited this bug was (maybe it was hardly exploited at all).
I always push for the open source community so it's disappointing that this has happened, but in some respects it shows the value of the Open Source community because they were able to pick it up - albeit extremely delayed.
Companies who use proprietary SSL software... It may be secure, it may not be. There is just no way for people to know so you're purely relying on them to be honest in their dealings.
I dont like quoting big chunks of text but that is a damn fine explanation. Cheers for that!
AtomicBlonde
Cancelled
Way over my head.
Ignorance - occasional bliss.
Ignorance - occasional bliss.

AussieHool
Senior List
Yes because since Friday I haven't been able to open Twitter on Chrome because of this.
Anyone know what I need to do to overcome this?
- Thread starter
- #11
The only thing I was really worried about was my Steam account, and I changed my password as soon as they fixed the issue.
What is a Steam account?
- Mar 25, 2003
- 35,681
- 28,334
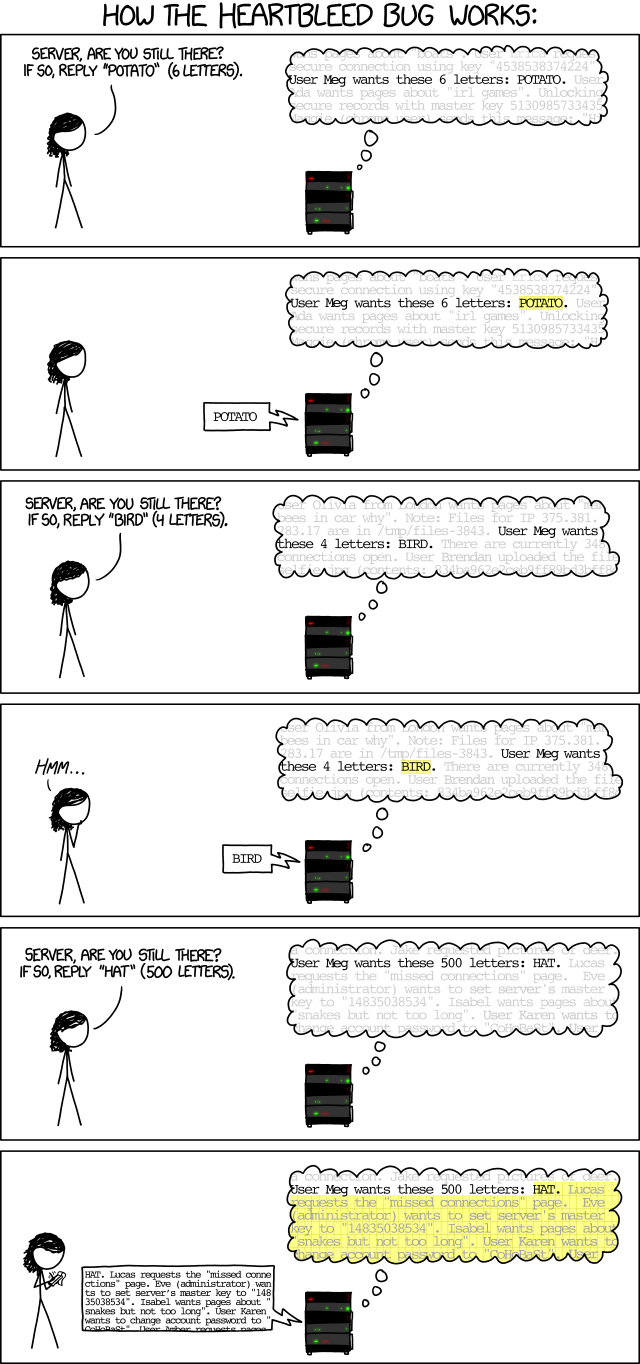
what i didn't address above is the bug itself. this is a little more technical but hopefully understandable.
SSL is a protocol. A protocol is a method of communication over a network. They one everyone is most familiar with is HTTP (Hyper Text Transfer Protocol) which is used to to serve websites. OpenSSL is an implementation of the SSL protocol that is widely used. OpenSSL is the only implementation effected by heartbleed, and only a specific version of OpenSSL (1.1). There are 3 stable versions of OpenSSL - 1.1, 1.0 and 0.9. From what I've read it's estimated 20% of HTTPS web sites on the internet are using OpenSSL 1.1.
As with any form of encryption SSL uses a key. Only the communicating devices know this key. You can think of it like a house key. Only you have the key to your house so only you can get in (legally). Same here - only the devices have the key so only they can encrypt and decrypt the messages back and forth.
This heartbleed bug is - under the right circumstances, which appear quite easy to replicate now that its known - leaking bits of memory from the OpenSSL application. This includes content, but most importantly the key a server is using to communicate with. It's only leaking 64kb at a time (each heartbeat as they are calling it) which isn't much but over time you could build a profile of a server and eventually replicate their cryptographic key which would enable you to impersonate the service.
SSL is a protocol. A protocol is a method of communication over a network. They one everyone is most familiar with is HTTP (Hyper Text Transfer Protocol) which is used to to serve websites. OpenSSL is an implementation of the SSL protocol that is widely used. OpenSSL is the only implementation effected by heartbleed, and only a specific version of OpenSSL (1.1). There are 3 stable versions of OpenSSL - 1.1, 1.0 and 0.9. From what I've read it's estimated 20% of HTTPS web sites on the internet are using OpenSSL 1.1.
As with any form of encryption SSL uses a key. Only the communicating devices know this key. You can think of it like a house key. Only you have the key to your house so only you can get in (legally). Same here - only the devices have the key so only they can encrypt and decrypt the messages back and forth.
This heartbleed bug is - under the right circumstances, which appear quite easy to replicate now that its known - leaking bits of memory from the OpenSSL application. This includes content, but most importantly the key a server is using to communicate with. It's only leaking 64kb at a time (each heartbeat as they are calling it) which isn't much but over time you could build a profile of a server and eventually replicate their cryptographic key which would enable you to impersonate the service.
your secret identity is safe with meDo you think our true identities will be revealed on BF?
What is a Steam account?
Collection of digital PC games. In my case, 400 of them. Not something I want stolen.
Another good password to change is Amazon, given it has credit cards linked to it.